App Features
Integrated Threat Detection: Cyvex offers a unified platform combining lightweight scanning, deep vulnerability audits, and external exposure analysis for a holistic security posture.
Modular Scanning Architecture: Supports thin client scanning, core network scanning, and optional plug-ins to target specific threat vectors with precision.
Automated External Risk Monitoring: Continuously monitors for domain breaches, credential leaks, and risky configurations across GitHub and Microsoft 365 environments.
Centralized Risk Visualization: Visual dashboards provide a real-time overview of threats, vulnerable assets, and sign-in anomalies to streamline response.
Efficient Endpoint Visibility
- Cyvex deploys a lightweight collector on end user devices to perform precise network discovery and vulnerability analysis with low system overhead.
- Detects active services, OS types, and open ports using Nmap to profile endpoints and surface potential risks.
- Uses Nikto to scan for insecure web server configurations, outdated software, and other exploitable weaknesses.
- Findings are instantly transmitted to the Cyvex platform, enhancing asset records and situational awareness.
Broad Spectrum Coverage
- Integrates optional scanners—OpenVAS, OWASP ZAP, WPScan, Lynis, clamscan, Nikto, Wapiti, and w3af—for in-depth analysis.
- OWASP ZAP, Wapiti, and w3af inspect dynamic behaviors, injection points, and access control weaknesses in web apps.
- Lynis and clamscan evaluate system hardening, malware presence, and compliance gaps in endpoint configurations.
- Findings are categorized into 'host audits' or 'vulnerability results' within the Cyvex platform for tracking and remediation.
Automated External Risk Monitoring
- Queries Have I Been Pwned to detect credential exposure events linked to organizational domains.
- Scans GitHub for mentions of sensitive internal identifiers, configuration tokens, and accidental code exposure.
- Inspects domain configurations for SPF, DKIM, and DMARC alignment to flag spoofing vulnerabilities.
- Identifies exposed secrets in environment variables or cloud stores, helping prevent privilege escalation.
Automated Risk Intake
- Integrates with GitHub Dependabot to retrieve CVE and dependency vulnerability alerts from linked repositories.
- Repository vulnerability data is pulled and updated every hour, ensuring near real-time risk awareness.
- Identifies impacted repositories, affected package versions, and unresolved alerts for targeted remediation.
- Enables DevSecOps alignment by mapping code-level risks into the Cyvex dashboard for unified tracking.
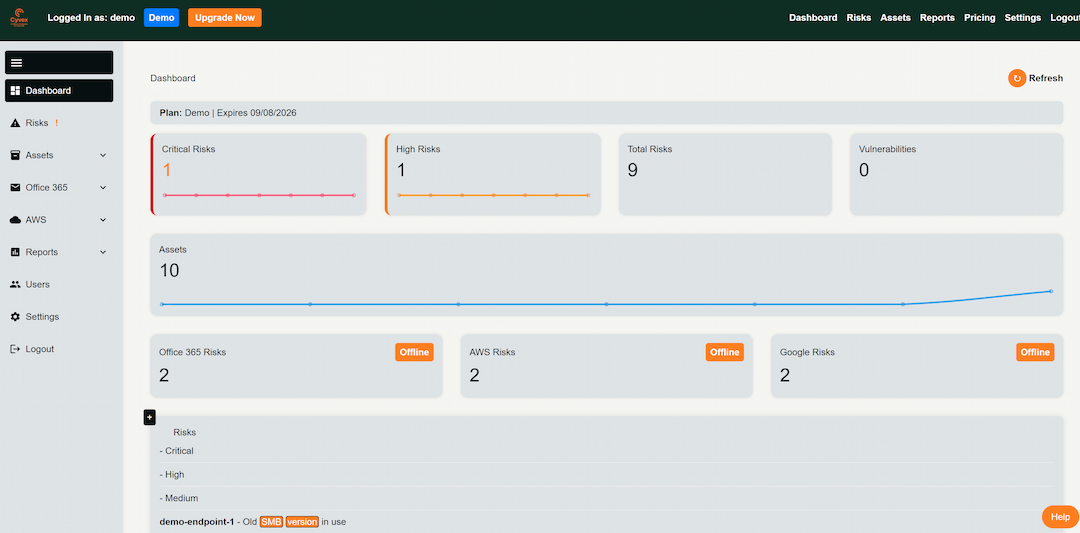

Secure Score Integration
- Retrieves Microsoft Secure Score to benchmark security posture and identify areas for hardening.
- Flags anomalous Office 365 login attempts based on geolocation, time of day, and account behavior patterns.
- Detects licensed users with inactivity, helping to deprovision unused access and reduce risk exposure.
- Audits Conditional Access, Intune compliance, and other settings to flag policy gaps.
Full-spectrum visibility: from endpoint scans to cloud configurations and developer workflows, Cyvex secures every layer of the attack surface.
